ATTENTION!
Encrypting data can serve to protect privacy or sensitive data, but it also means that manual decryption can make it more difficult to recover any data that may be required in the future. A decision for or against data encryption should therefore not be made lightly. An individual risk-benefit analysis based on the application area, the user’s computer skills or similar factors is recommended in order to minimize the risk of subsequent data loss.
The Ubuntu system can be encrypted since Ubuntu 12.10 already automatically during installation. This guide installs Ubuntu by manual instead of automatic partitioning in an encrypted area, so you have influence on the partitioning. As with the automatic installation, the boot partition, and with a UEFI system additionally the EFI partition, remains unencrypted. Only the boot loader and kernel are located here because the boot loader cannot read any data from the encrypted area.
The Logical Volume Manager is used, because with it only one password entry is necessary at startup, the hibernation (S4) still works and it is very flexible as far as partitioning is concerned.
Alternatively, it is also possible to encrypt the system without LVM, but this variant is less flexible as far as subsequent partition changes within LVM are concerned. It is also possible to encrypt the system with the non-graphical installation, which is the option of choice if no Internet connection is available.
Preparations
Note:
All of the following commands require root privileges. So you should either always put sudo in front of the command in question or use sudo -s to gain root status!
If the computer already has an operating system (such as Windows, Mac OS or other Linux system) or important data, it is essential to create a backup of the important data. As with any change to the computer, something can always go wrong.
The normal desktop CD is required for installation. Simply boot this . After the live system has been loaded, do not run the installation program but start the trial version. It is mandatory to have a working Internet connection, because programs must be installed.
Load software and kernel modules
In older versions, the desktop CD does not natively support . However, at least since 13.10, support is present. For older versions you can correct this by installing the following package:
- lvm2
Package list for copying:
sudo apt-get install lvm2
Or install with apturl.
Partitioning
Note:
/dev/sdX1 bzw. /dev/sdX2 must always be replaced by the actual designation of the partition in the following!
Two partitions are required:
- /dev/sdX1 (ext4)
- Boot partition (unencrypted)
- Size: at least 250 MB (to leave room for 4 kernels, more detailed explanation under Manual Partitioning (section „Preliminary Considerations“))
- /dev/sdX2 (unformatted)
- encrypted LVM volume
- Size: usually the available rest, but at least 8 GB (root + memory)
Expert Info:
One should inform oneself in advance whether the computer is provided with an EFI boot management and how the hard disk(s) were formatted! Further information is available under EFI basics!
It should be noted that an unencrypted EFI partition must always be created in addition to the unencrypted boot partition on EFI systems. An alternative would be to use the BIOS compatibility mode CSM.
Encryption of the partition
ATTENTION!
For security reasons, it is recommended to overwrite the partition once with random numbers, especially if unencrypted data was previously stored on it. Otherwise, many files may still be readable after encryption.
A LUKS medium is then created in the large partition and then opened with the name lukslvm . When using with 256 bit the commands look like this:
cryptsetup luksFormat -c aes-xts-plain64 -s 512 -h sha512 /dev/sdX2
cryptsetup luksOpen /dev/sdX2 lukslvm XTS requires a management key with a length of 128 or 256 bits. The length of the management key must be added to the key length. Thus, total key lengths of 256, 320, 384, 448, or 512 bits are possible with AES.
Creation of the LVM partitions
The following commands create the LVM volume in the encrypted partition.
pvcreate /dev/mapper/lukslvm vgcreate vgubuntu /dev/mapper/lukslvm
In a standard installation of Ubuntu, two partitions are created, one for the swap space – usually about 1.3 times the RAM, so with 1024 MB of RAM, just under 1300 MB – and one for the root file system with the remaining space. These are created as logical volumes as follows:
lvcreate -L 1300M -n swap vgubuntu lvcreate -l 100%FREE -n root vgubuntu
If more partitions are needed, they can be set up in the same way. Of course, 100% of the available space must not be allocated for root.
Wegen Problemen mit dem Live-CD-Installer müssen alle Partitionen vorher manuell formatiert werden. Mit der Option -L name kann der Partition noch eine Bezeichnung (Label) gegeben werden:
mkswap /dev/mapper/vgubuntu-swap -L swap mkfs.ext4 /dev/mapper/vgubuntu-root -L root
Installation

Afterwards the installation program is started and continued with this until selection of the partitioning, where the „manual partitioning“ is selected.
In the next installation point, the following partitions are each configured by double-clicking on the corresponding entries. The swap partition does not need to be selected because it is detected automatically.
- /dev/sdX1
- Boot-Partition
- File system: ext4
- Format: „yes“
- Suspension point: /boot
- /dev/mapper/vgubuntu-root
- Root-Partition
- File System: ext4 or desired Linux file system
- Format: „jyesa“
- Suspension point: /
Make sure that the boot loader is installed on a meaningful device outside the encrypted container, for example, the master boot record of the hard disk („Device for Bootloader installation:“ /dev/sdX). Then proceed with the installation according to the instructions, but do not reboot after the installation is complete.
ATTENTION!
Any changes made to partitions can no longer be undone!
Expert Info!
If Windows was installed in parallel and encrypted with VeraCrypt, GRUB must be installed in the boot partition /dev/sdX1 instead of the MBR. This must be set in the installation point 7 under „Advanced“. There the boot partition must be selected instead of hd0. GRUB then appears as soon as Esc is pressed in the VeraCrypt boot loader.
With EFI boot management it does not matter which setting you choose for the boot loader. It is always installed in the EFI partition. However, you must assign the EFI boot partition selection to the EFI partition.
Switch to the encrypted system
NOTE:
All the following commands must be executed in one and the same terminal.
To make the necessary adjustments, chroot is used to switch to the actual, encrypted system. This is done by entering the following commands. It should be noted that if you have created additional partitions, such as /var, you must also mount them appropriately before issuing the chroot command.
# root Filesystem
mount /dev/mapper/vgubuntu-root /mnt
# boot Filesystem
mount /dev/sdX1 /mnt/boot
# Notwendige system-interne Filesysteme
mount -o rbind /dev /mnt/dev
mount -t proc proc /mnt/proc
mount -t sysfs sys /mnt/sys
# Zusätzliche LVM Verzeichnisse (notwendig bei 15.10, evtl. auch hilfreich bei früheren Releases)
mount -o rbind /run/lvm /mnt/run/lvm
mount -o rbind /run/lock/lvm /mnt/run/lock/lvm
# DNS-Auflösung im verschlüsseltem System ermöglichen
cp /etc/resolv.conf /mnt/etc/resolv.conf
# In das verschlüsselte System wechseln
chroot /mnt /bin/bash Bei EFI Bootmanagement muss Zeile 2 durch die beiden folgenden ersetzt werden:
mount /dev/sdX2 /mnt/boot
mount /dev/sdX1 /mnt/boot/efi Usually the EFI partition is sdX1, which is followed by the boot partition /mnt/boot with sdX2.
Install software
The required packages are installed with this command:
apt-get install cryptsetup lvm2
/etc/crypttab edit
Note:
If necessary, the /etc/crypttab file does not yet exist. The compact method described below makes it easy to create it.
Basically, the crypttab is structured as follows:
| 1 | <target name> <source device> <key file> <options> |
First, the UUID of the encrypted partition or LVM volume must be determined. This is done with the following command:
blkid /dev/sdX2
This input is then used to insert the necessary line in /etc/crypttab, where must first be replaced by the determined UUID. The UUID must be entered without quotes in /etc/crypttab (i.e. xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx instead of „xxxxxxxx-xxxx-xxxx-xxxxxxxxxxxx“). If a name other than lukslvm was specified previously when opening the encrypted partition with luksOpen, then exactly this name must be entered – if the entry in /etc/crypttab differs from the currently used name, the partition cannot be decrypted when rebooting:
echo "lukslvm UUID=<VOLUME_ID> none luks" >> /etc/crypttab Newer versions of cryptsetup can also determine the UUID themselves:
cryptsetup luksUUID /dev/sdX2 or compact:
printf "lukslvm\tUUID=%s\tnone\tluks\n" "$(cryptsetup luksUUID /dev/sdX2)" | tee -a /etc/crypttab Edit /etc/modules
Now the dm-crypt module must be added under /etc/modules if it does not already exist there:
echo "dm-crypt" >> /etc/modules Update kernel initramfs
To apply the changes to the crypttab, you still need to add
update-initramfs -u -k all to be executed.
Update/check GRUB configuration
NOTE:
„data journaling“ (or also „full journaling“) is not to be confused with „metadata journaling“, see Journaling file systems and Mount options for ext3 🇬🇧 (option „data“, especially with the value „data=journal“).
If the root partition is to be mounted with „data journaling“ enabled, a corresponding kernel parameter must already be specified at kernel startup. The entry in /etc/fstab is then no longer sufficient because this file can only be read when the root file system has already been decrypted and mounted in the system. Under /etc/default/grub, one edits the GRUB file as follows:
| 1 | GRUB_CMDLINE_LINUX_DEFAULT=“kopt=root=/dev/mapper/vgubuntu-root“ |
After that, you need to update Grub:
update-grub Exit/Restart
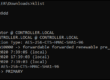
The following commands close the chroot environment, unmount the file systems as far as possible, and reboot the system. The installation media (USB stick or DVD) must be removed and the subsequent boot process should then ask for the LUKS password.enlarge
Exit the encrypted system exit write buffer for data medium sync remove "mounted" file system again umount /mnt/run/lvm umount /mnt/run/lock/lvm umount /mnt/sys umount /mnt/proc umount /mnt/boot/efi # only necessary for EFI systems umount /mnt/boot # swapoff -a # reboot
Change password
The password entered by the user only decrypts a master key, which is ultimately used for the security of the file system. The LUKS used here thus makes it possible for the password to be changed easily without having to re-encrypt the entire file system. The master key ultimately remains the same. It is even possible to use multiple keys (up to 8) at the same time, the master key is then simply available multiple times with the password used in each case, with the password query then only the respective slot must be able to be unlocked.
Note:
In the event of an attack on the encrypted system, it is already enough to decrypt one slot. It is therefore important to ensure that all passwords used are sufficiently secure. It makes sense to use multiple passwords, especially for a multi-user system. Alternatively, you can set a second password in case you forget the password you actually used. You can also store the same password in another slot to protect yourself from file system errors in one of the slots.
Add key
The following command adds a key to the specified drive:
cryptsetup luksAddKey /dev/sdX2
Remove key
ÁTTENTION!
Here you can lock yourself out of the system if you are not careful. When changing a password, first create the desired password, test it if necessary, and only then delete the old password.
The following command removes the key entered below:
cryptsetup luksRemoveKey /dev/sdX2
Show information
Output overview of the LUKS header
The following command outputs an overview of the information contained in the LUKS header of the encrypted partition. This makes it possible to see, for example, how many of the 8 key slots are already occupied and which are still free. Also information is given about which encryption method is used for this partition, as well as some further information, e.g. also about the already above mentioned UUID.
cryptsetup luksDump /dev/sdX2
Check whether the TRIM command is passed through
If you want to check whether the TRIM command, which can be useful for SSDs, is passed through for a LUKS partition, this can be checked with the following command.
cryptsetup status /dev/mapper/lukslvm
Note that in this example, cryptsetup is applied to the LVM partition and not to /dev/sdX2. If the option „discards“ is then displayed next to the „flags“ field, then the trim command is passed through. If not, then TRIM must still be activated accordingly, if you want to use TRIM, see SSD/TRIM.
ATTENTION!
Using the TRIM command in conjunction with LUKS encryption can be a security risk. More about this can be found in the following article: SSD/TRIM (section „TRIM-with-Disk-Encryption“).
Startup problems
If only individual partitions are encrypted and are to be mounted at startup, the user is offered to cancel the mount before the key can be entered. To prevent this, add the following to /etc/init/mountall.conf behind
| 1 2 3 | # temporary, until we have progress indication # and output capture (next week :p) console output |
enter the following code block:
| 1 2 3 4 5 6 7 8 9 10 11 12 | pre-start script . /lib/cryptsetup/cryptdisks.functions case „$CRYPTDISKS_ENABLE“ in [Nn]*) exit 1 ;; esac INITSTATE=“init“ do_start end script |
This causes the system to wait until the code entry is complete.
Alternative – Installation mit Hilfe eines Skripts
https://gist.githubusercontent.com/HoffmannP/699f3beb2f9901cd64e8/raw/322e29a6a4c8d9261b882fb8e4b968388d58fb06/full-disk-encryption-lvm-luks%25202 🇬🇧 is an open source shell script that can also install a fully encrypted Ubuntu system via LUKS/LVM. The semi-automatic script makes one’s work easier, since no complicated command sequences have to be entered. In addition, it only takes a few minutes longer to install a fully encrypted system compared to a standard installation.
NOTE!
Fremdsoftware kann das System gefährden.
Sollte man sich für diese Methode entscheiden:
- Boot from USB to start a live session.
- Download and run the script. Just open a terminal and execute the following commands (copy and paste recommended):
wget "https://gist.githubusercontent.com/HoffmannP/699f3beb2f9901cd64e8/raw/322e29a6a4c8d9261b882fb8e4b968388d58fb06/full-disk-encryption-lvm-luks%25202" -O "/tmp/ubuntu-full-disk-encryption-lvm-luks.sh"
chmod a+rx /tmp/full-disk-encryption-lvm-luks.sh
/tmp/full-disk-encryption-lvm-luks.sh - Follow the instructions of the script.
If you are interested in the background, you can find a detailed description in the article Fully encrypted system with Ubuntu (from 9.04 Jaunty), LVM and LUKS 🇩🇪.
Alternative decryption of the system partition with a USB key
If you want to decrypt the system with the help of a USB stick (without having an obvious key file on said stick, the stick can therefore also be formatted arbitrarily), the article Decrypting with a USB key will help.